In today’s digital age, our smartphones serve as gateways to a vast amount of information and services. However, this convenience comes with inherent risks, particularly in the form of phishing scams. These deceptive attacks aim to steal your sensitive personal information, including usernames, passwords, credit card details, and even social security numbers. Protecting yourself from phishing scams is crucial to maintaining your online security and privacy. This article will provide you with essential knowledge and practical tips to safeguard your smartphone and personal data from these malicious threats. Understanding how to identify and avoid phishing attempts is the first line of defense against becoming a victim.
Phishing attacks on smartphones are becoming increasingly sophisticated, making it harder than ever to distinguish legitimate communications from fraudulent ones. Criminals employ various tactics, such as smishing (SMS phishing) and vishing (voice phishing), to trick unsuspecting users. They often impersonate trusted organizations like banks, government agencies, or popular online services, creating a sense of urgency or fear to coerce victims into taking immediate action. By learning to recognize the common signs of a phishing scam, you can empower yourself to protect your valuable information and avoid falling prey to these cybercriminals. This article will detail specific methods to identify phishing attacks, such as scrutinizing suspicious links, verifying sender identities, and being wary of unsolicited requests for personal information.
Recognize Suspicious Links
One crucial step in protecting yourself from phishing scams is learning to identify suspicious links. Phishing attacks often rely on deceptive links that appear legitimate but lead to fraudulent websites. These websites mimic real login pages or offer enticing deals to trick you into revealing sensitive information.
Pay close attention to the URL. Look for misspellings, unusual characters, or shortened URLs. Legitimate websites, especially those handling sensitive data, will typically have secure, recognizable domain names. Be wary of URLs that seem overly long or complex.
Hover your cursor over the link before clicking to see the actual destination. This preview can often reveal the true nature of the link. If the destination doesn’t match the displayed link text, it’s a strong indicator of a phishing attempt.
Be especially cautious of links received via email, text messages, or social media. Avoid clicking on links from unknown or untrusted sources. It’s safer to type the website address directly into your browser if you have any doubts about a link’s legitimacy.
Use Anti-Phishing Apps

Anti-phishing apps provide an additional layer of security against phishing attacks. These apps typically work by scanning websites and messages for suspicious content, comparing them against known phishing databases, and alerting you to potential threats. They can integrate with your browser and messaging apps to offer real-time protection.
Several reputable anti-phishing apps are available for both Android and iOS devices. Research and choose an app that fits your needs and has positive user reviews. While these apps can be highly effective, they should be used in conjunction with other security measures, not as a standalone solution.
Key benefits of using anti-phishing apps include:
- Real-time protection: Receive alerts before interacting with potentially malicious content.
- Phishing database checks: Apps cross-reference websites and messages with known phishing databases.
- Browser and messaging integration: Seamless protection across various platforms.
Avoid Public Wi-Fi Traps
Public Wi-Fi hotspots are convenient, but they often lack robust security measures. This makes them prime targets for cybercriminals seeking to intercept your data.
When connected to public Wi-Fi, avoid accessing sensitive information such as online banking, email accounts, or social media profiles. If you must use public Wi-Fi, consider using a virtual private network (VPN). A VPN encrypts your internet traffic, making it much more difficult for hackers to eavesdrop.
Be wary of fake Wi-Fi hotspots. Attackers sometimes set up rogue hotspots with names similar to legitimate networks (e.g., “Coffee Shop Free Wi-Fi” instead of “Coffee Shop WiFi”). Always verify the network name with staff before connecting.
Enable Email Filters
Most email providers offer built-in spam and phishing filters. These filters analyze incoming emails for suspicious characteristics, such as malicious links, suspicious senders, and phishing keywords. Enabling and configuring these filters can significantly reduce the number of phishing emails that reach your inbox.
Activating these filters is usually a simple process, often involving checking a box or selecting a security level in your email account settings. Some providers offer advanced filtering options, allowing you to customize the filters to your specific needs. For example, you can create rules to automatically block emails from certain senders or containing particular keywords.
While these filters aren’t foolproof, they represent a crucial first line of defense against phishing attacks. Regularly reviewing your spam or junk folder can also help identify phishing attempts that manage to bypass the filters. If you spot a suspicious email, be sure to report it as spam or phishing to your email provider. This helps improve the accuracy of the filters and protects other users.
Report and Block Scammers
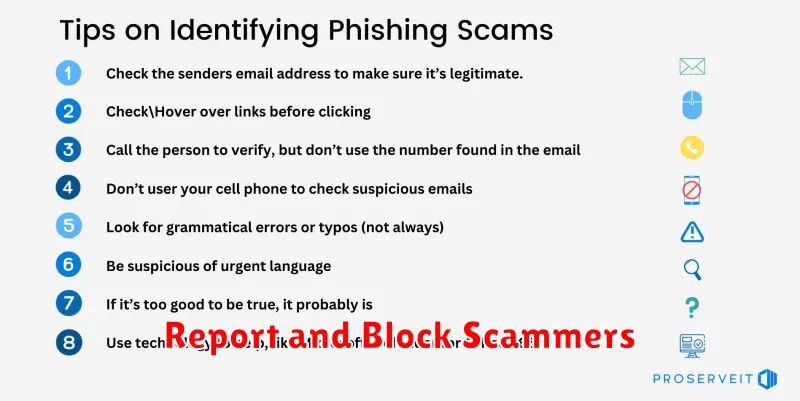
Taking proactive steps to report and block scammers is crucial in protecting yourself and others. Reporting these malicious actors helps authorities track their activities and potentially shut down their operations. It also contributes to a safer online environment for everyone.
Reporting suspected phishing attempts is essential. Contact your wireless carrier immediately. You should also report the incident to the Federal Trade Commission (FTC) through their online portal or dedicated phone number. If the scam involved a specific company or organization, notify them as well. Provide as much detail as possible, including the phone number, message content, and the date and time of the contact.
Blocking the scammer’s number prevents further unwanted contact. This is a simple process on most smartphones. Access your recent calls, select the number, and choose the option to block or add to your reject list. Regularly review your blocked numbers list and remove any entries as needed.

